Best Practices for Implementing Mobile App Management (MAM)

Summary:
Organizations need to manage mobile apps securely and efficiently without compromising employee productivity. Mobile App Management (MAM) offers a powerful solution by allowing IT teams to control and secure corporate apps and data on both company-owned and personal (BYOD) devices, without managing the entire device.
This blog dives into the best practices for implementing MAM successfully, helping businesses protect sensitive information while supporting flexible, mobile workforces. You’ll learn how to assess your organization’s mobility needs, choose the right MAM solution, set up app-level security policies, integrate with identity and access management systems, and provide end-user training.
Whether you’re starting from scratch or optimizing an existing system, this guide will help you roll out MAM in a way that enhances security, simplifies app deployment, and aligns with your overall enterprise mobility strategy.
Introduction
As the modern workplace becomes increasingly mobile, organizations face the challenge of getting commercial data into the increasing number of smartphones and tablets, many of which are personally owned by employees. This shift has made Mobile App Management (MAM) an important component of Enterprise Mobility Strategies.
Unlike Traditional Mobile Device Management (MDM), which controls the entire device, MAM focuses especially on the data managed and secured, and access to it. This approach allows companies to support their unity policies while controlling sensitive information.
However, MAM requires more than installing only software to search effectively. This includes a thoughtful strategy, clear guidelines, and the right tools to ensure safety and user productivity. In this blog, we will find out the best practices to implement Mobile App Management (MAM), which range from choosing the right solution to rolling out the organization.
Understanding Mobile App Management (MAM)
How employees access and use business apps on their equipment is important. Mobile App Management (MAM) allows organizations to control, secure, and monitor business apps and data without managing the entire device. It is especially useful in BYOD scenarios, where individual and business use overlap.
MAM enables companies to implement app -specific security policies, including certification, encryption, remote and access control, and ensure that sensitive data is preserved regardless of the device used, ensuring sensitive data is preserved. In order to implement MAM successfully, it is necessary to have apps that are customized for protection against corporate control and basis.
That’s where partnering with a trusted mobile app development company can make all the difference. These companies can produce customized mobile applications designed for MAM compatibility, which helps your business implement security policies by providing a spontaneous user experience. Whether you develop internal tools or customer-facing apps, and work with the right development partner, your apps are sure to match your mobility strategy and compliance requirements.
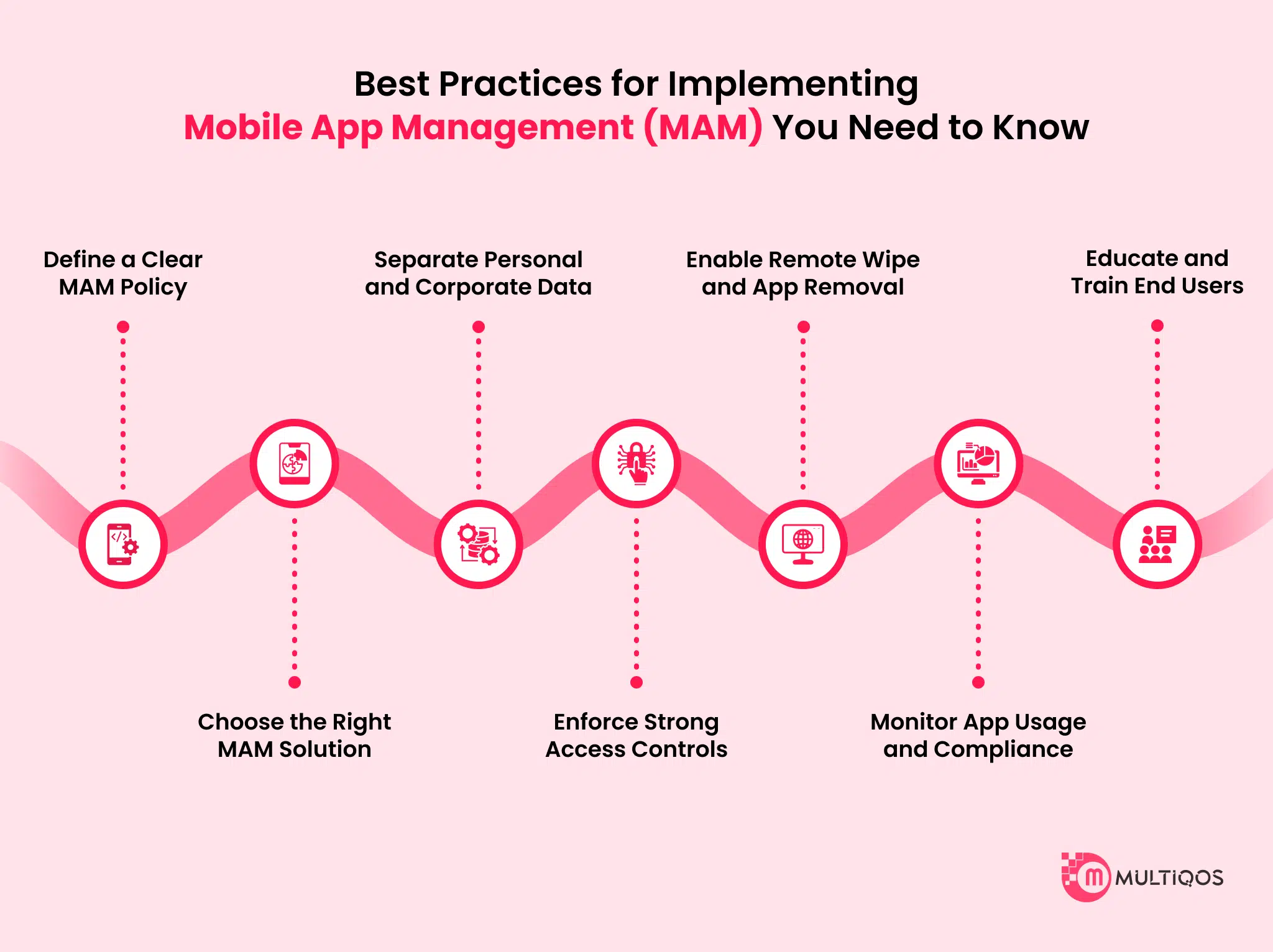
Best Practices for Implementing Mobile App Management (MAM) You Need to Know
With the emergence of external work, BYOD policies, and mobile-first strategies, Mobile App Management (MAM) has become the cornerstone of modern corporate security. This gives organizations the right to control, secure, and manage mobile applications and their data without full control of users’ equipment. To implement MAM and prepare you for the future of mobile app development, there are seven best practices you need to follow:
1. Define a Clear MAM Policy
Before using a MAM solution, it is important to create a well-defined policy that determines the basis for safe app use. This policy should emphasize which apps are approved, how business data is handled, and what security protocols are implemented. To determine and ensure compliance with expectations, you clearly communicate this policy to employees. A strong policy not only supports security but also adjusts MAM to widespread business purposes.
2. Choose the Right MAM Solution
Not all mam equipment is the same. Evaluate MAM solutions based on scalability, compatibility with existing infrastructure, support for platforms, and integration options. Choose a solution that matches the organization’s security goals and provides flexibility for your users. Choosing the right platform for Mobile App Management (MAM) is important for long-term success and supports close growth processes involved in modern mobile app design strategies.
3. Separate Personal and Corporate Data
One of the biggest benefits of MAM is the ability to maintain a strict distinction between individual and corporate data, especially in the BYOD environment. Use container and app-level encryption to protect the data related to work without violating a user’s privacy. This separation is not just a safety measure; it also boosts employee confidence and enhances the user experience.
4. Enforce Strong Access Controls
Secure access is important. Use strong access control mechanisms within the MAM framework, such as Single Sign-On (SSO), Multi-Factor Authentication (MFA), and access to health or location. These properties ensure that only authorized users can access sensitive apps and data, which can reduce the risk of breaches and data leaks.
5. Enable Remote Wipe and App Removal
In the event of a lost device, employee departure, or safety hazard, your mobile app management (MAM) solution should allow you to wipe away from a distance or disable the specific app. This targeted approach helps you protect sensitive corporate data without exterminating personal information, which is especially important in a BYOD landscape. Distance management is an important component of active risk reduction.
6. Monitor App Usage and Compliance
Mobile app management (MAM) equipment provides visibility into how apps are used in your organization. Monitor compliance with regular app usage patterns, user behavior, and guidelines. This data can help the IT teams recognize deviations or potential threats quickly and take corrective measures before the problems occur. Proactive monitoring also helps ensure that your MAM guidelines remain effective as technology develops.
7. Educate and Train End Users
Technology alone is not enough; Users should understand how they use MAM safely and responsibly. Provide running and resources to help employees understand MAM guidelines, what to do in the event of an issue with a device, and how to handle sensitive data. Well-informed users are the first row of your protection and are important for successful MAM adoption.
Wrapping Up
Using Mobile App Management (MAM) is no longer optional for organizations aimed at being safe and productive in the mobile-first world. By choosing the right tools to set clear guidelines and training of final users, to ensure best practices, ensure a smooth distribution, and long-term success.
By focusing on app-tier security, supporting the city environment, and integrating with its existing IT infrastructure, your mobile app management (MAM) team strengthens a flexible compromise on data security.
To ensure that your MAM strategy is not only safe but also scalable and user-friendly, it is necessary to build or adapt apps with management. This is why many companies choose to hire mobile app developers who understand business mobility and can design apps that align with your MAM guidelines.
FAQs
MDM manages and secures the entire device, while mobile app management (MAM) just focuses on managing and securing specific apps and their data. MAM is more flexible and suitable for privacy, which makes it ideal for urban and hybrid functional environments.
MAM helps protect sensitive commercial data, ensures observance of security policy, supports productivity in different devices, and reduces the risk of data leaks, especially when employees work at a distance or use individual equipment.
Yes. MAM is specially designed to work in BYOD settings by securing business apps and data without disrupting individual apps or users’ privacy.
By checking access to MAM business data, helping the use of the app helps and allows distance data wipes if necessary to apply data security policies (for example, GDPR or HIPAA), without managing all individual devices.
Get In Touch