Zero Trust Architecture: The Complete Guide 2025

What is Zero Trust Architecture?
Zero Trust Architecture is the security model that takes the device or user into consideration that they are under potential threat, be it inside the network or outside. Using this model, one can verify and authenticate user, device, and network requests before granting access to any of the sensitive resources.
Zero Trust is designed to prevent unauthorized or unauthenticated access to applications, sensitive data, and systems. Overall, it provides an end-to-end comprehensive security framework that puts weight on the need for real-time threat detection, constant monitoring, and adaptive access to control policies. Some of the popular zero trust architectures are AWS zero trust architecture, and Azure zero trust architecture. Each of them offers its own set of features.
History of Zero Trust
The Zero Trust Security was introduced back in 2010 by the former Forrester Research Analyst, John Kindervag. During that time, any traditional parameter-based security model was not efficient enough and was failing to protect any of the sensitive data from cyber threats or any other. His idea was to bring a new security paradigm, that “ner trust, always verify” rather than verify”/ this approach has challenged some of the conventional approaches that all devices, users, and network traffic are trustworthy inside the parameter.
As more and more companies are now adopting cloud services, mobile devices, and remote work, the Zero Trust architecture has gained a lot of momentum. There are a lot of technology companies like Amazon, Microsoft google, and many more offering the Zero Trust Architecture to the users.
Microsft zero trust architecture offers Azure Active Directory (AAD), and Azure Information Protection (AIP), while zero trust architecture AWS offers various components like AWS Identity Access Management (IAM) and Amazon Virtual Private Cloud(VPC). These solutions utilize all the zero trust architecture principles to secure and sensitive applications and their data.
Foundations of the Zero Trust Model
There are a few foundational principles based on which Zero Trust Model is built. A few of the key principles are listed below.
- Multifactor Authentication: users should need to provide more than one authentication factor to access the application or the resources.
- MicroSegmentation: Networks in the application should be segmented into smaller zones and access should be given on basis of zones.
- Least Privilege Access: Devices and Users should have access to only specific resources that are required to perform certain tasks.
- Continuous Monitoring and Analytics: Real-time monitoring and analytics need to detect potential threats and anomalies.
Also Read: How to Develop a Cloud-Based Application?
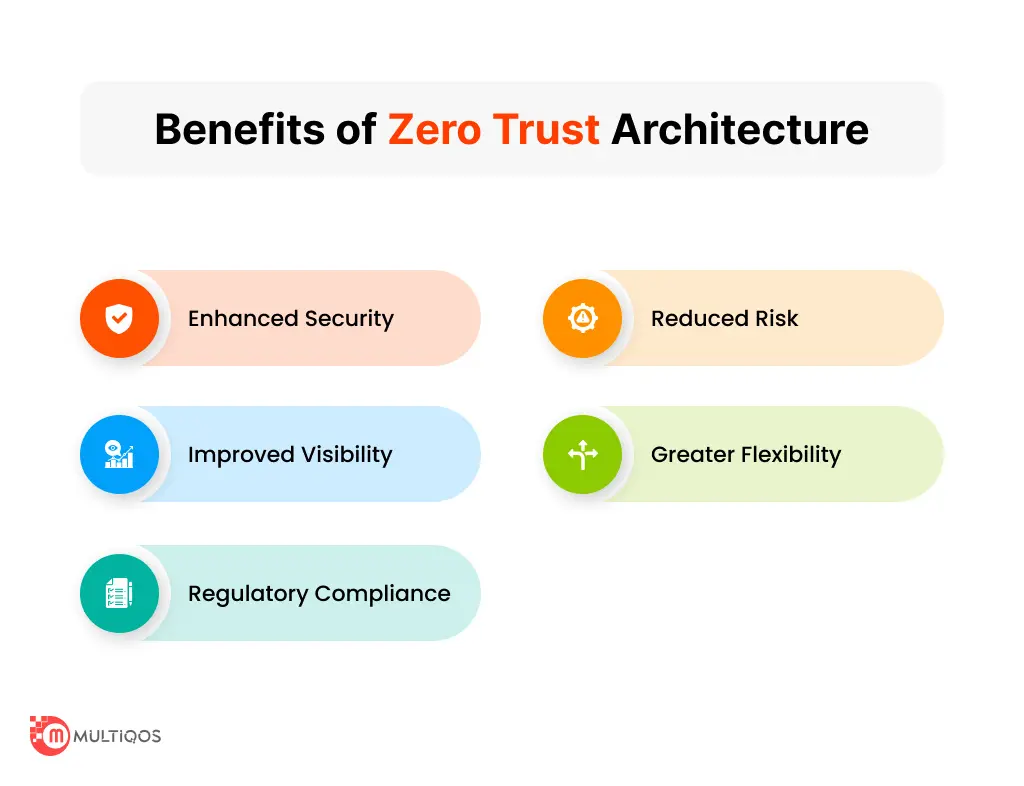
Benefits of Zero Trust Architecture
A few of the benefits of Zero Trust Architecture are given below.
- Improved Security: Zero Trust Architecture needs an effective and comprehensive security model than the conventional perimeter-based security models.
- Reduced Risks: Assuming all the devices and users are untrusted, Zero Trust Architecture reduces the chances of unauthorized or unauthenticated access tot he sensitive applications and data.
- Enhanced Visibility: Real-time monitoring and analytics offer greater visibility into potential threats and network traffic.
- Increased Compliance: Zero Trust Architecture helps organizations to meet compliance requirements by offering an auditable and secure access control framework.
- Better Response to Incidents: With real-time data monitoring and analytics, Zerot Trust Architecture helps to respond faster to security incidents.
Reasons Why Enterprises need Zero Trust Architecture
There are several reasons why Enterprises need Zero Trust Architecture.
- As technology gets more advanced the threat landscape is also changing. With the proliferation of cloud services, remote work, and mobile devices, the conventional perimeter-based security model is not sufficient enough.
- High Rate of Data breaches: Apparently lot of Data breaches are happening nowadays, and the cost of data breaches can be significantly quite high.
- Increased Remote Work: the Pendamic has given rise to the trend of remote work that needs a robust security model.
- Regulatory compliance firms demand a comprehensive security model. Enterprises need to comply with HIPPA or GDPR like regulation companies.
The Future is Zero Trust
The current scenario demands a secured architecture and zero trust architecture fulfills the need. Enterprises are now constantly exploring and leveraging the trend of remote work, mobile devices, and cloud services. Hence the need for a comprehensive security model assuming no trust is quite crucial. Zero Trust Architecture provides all the features that protect sensitive systems and data. Some of the primary features are encryption, network segmentation, endpoint security, identity, and access management.
If you are looking to explore more Zero Trust architecture and want to integrate it into your application, you can consult with a Mobile app development company in india. A professional mobile app development company would assess your risk profile, evaluate your security needs, and design and implement zero-trust architecture for Microsoft, AWZ, or Azure. With the right approach and guidance, you can leverage zero trust architecture to improve the security of the applications and protect it from any business threats.
Implement Zero Trust in your business today with our plan.
Our expert developers are ready to provide you with a customized Zero Trust implementation plan for your business.
FAQ about Zero Trust Architecture
The primary goal of Zero trust architecture is to provide an effective and comprehensive security model which assumes that all the devices, users, and network traffic are untrusted and need to very and authenticate themselves before getting access to any sensitive resource.
The key principles of Zero trust Architecture are continuous monitoring and analysis, micro-segmentation, multi-factor authentication, and least privilege access.
There are many advantages of implementing the zero trust architecture, some of them are cyber attacks, data breaches, increased visibility into the network, and simplified compliance with regulations.
Some of the primarily used components for Zero trust architecture are multifactor authentication (MFA) solutions, Idenity and access management (IAM) solutions, and continuous monitoring and analytics platform.
Yes, Zero trust Architecture is efficient for all the different types of organizations regardless of their security requirements, industry, and size. If you want to get a tailormade solution then you can also avail the software development services.
Get In Touch