Top Security Challenges in Enterprise Software Development and How to Overcome Them

Summary:
Security remains one of the most critical challenges in enterprise software development. This blog explores the top security risks organizations face, such as data breaches, insecure APIs, and poor access controls, and provides actionable solutions.
We highlight the best strategies to protect enterprise applications, from implementing robust encryption to adopting secure coding practices and regular vulnerability assessments. Whether you’re a developer, IT leader, or decision-maker, this guide will help you navigate the key security challenges in enterprise software development and build safer, more resilient systems.
Introduction
As businesses advance in the present day of swift technological innovation, enterprise software development faces multifaceted security issues. For example, when companies scale their operations, they start handling greater volumes of sensitive data which increases the risk of severe repercussions due to software vulnerabilities. Organizations face a myriad of risks beyond mere data leaks and internal terrorism. The scope of threats includes strategic, compliance, and significant fiscal threats.
This blog analyzes the most important security challenges in enterprise software development businesses face during the development life cycle and describes optimal approaches to mitigate them. As a developer, technology executive, or organizational strategist, knowing these challenges and their resolutions is essential for constructing effective, secure, and reliable applications.
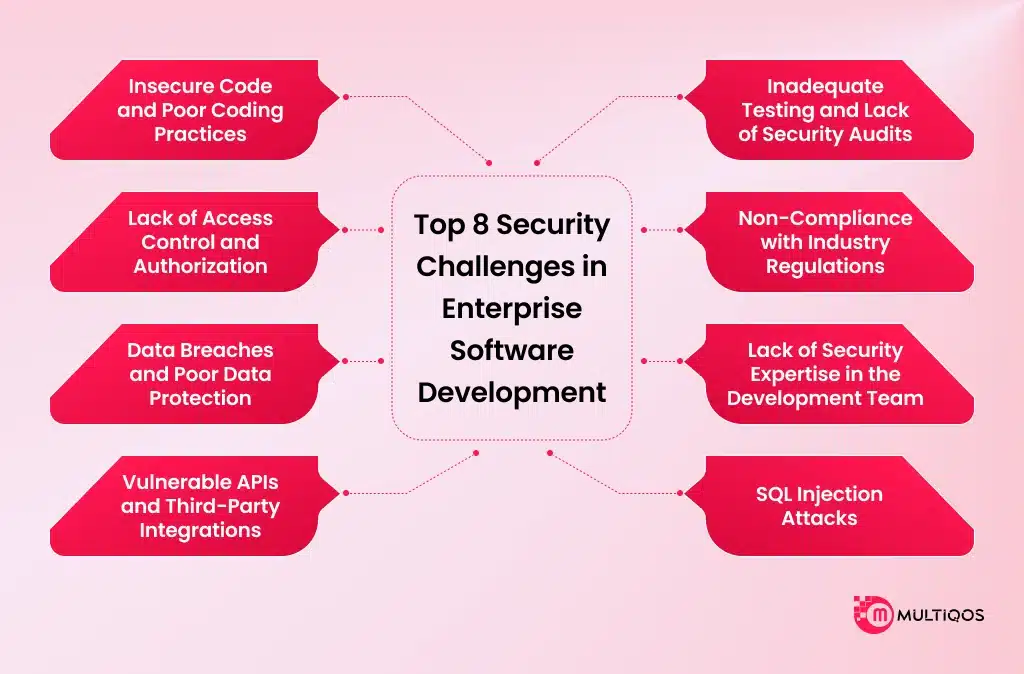
Top 8 Security Challenges in Enterprise Software Development
1. Insecure Code and Poor Coding Practices
Challenge:
Security vulnerabilities arise especially from insecure code, which may be a product of obsolete libraries, substandard input sanitization, or an absent secure programming policy.
Solution:
Across the team, implement secure coding policies. Perform periodic code reviews and run SAST tools to STASH vulnerabilities in the code early on. Educating developers on secure software development practices further strengthens a culture of security.
2. Lack of Access Control and Authorization
Challenge:
Inadequate access controls may result in privilege escalation and/or access to confidential data or functions without authorization.
Solution:
Apply user permissions according to the principle of least privilege (PoLP). Secure user identity and access at all levels by assigning access through role-based access control (RBAC) alongside multi-factor authentication (MFA).
3. Data Breaches and Poor Data Protection
Challenge:
Sensitive information relevant to an enterprise is most vulnerable when it is not well-secured or adequately encrypted, making it easy for attackers to target.
Solution:
Ciphers of industry-standard algorithms must be applied to all data stored and all data transferred. Use secure databases, and implement tokenization or data masking techniques as suited. Regular data backups should be made alongside thorough disaster recovery plans.
4. Vulnerable APIs and Third-Party Integrations
Challenge:
When trusting third-party services, open or inadequately safeguarded APIs are frequently misused as attack vectors.
Solution:
Make sure that proper authentication is done on your APIs and that rate limiting is configured. Conduct security reviews of the external utility’s software and check that all integrations meet your organization’s security framework.
5. Inadequate Testing and Lack of Security Audits
Challenge:
Numerous security gaps will go unnoticed until devastating harm has been inflicted.
Solution:
Perform both manual and automated tests, such as penetration tests, dynamic application security tests (DAST), and vulnerability scans. Incorporate periodic security audits and compliance reviews into the development lifecycle.
6. Non-Compliance with Industry Regulations
Challenge:
You can really damage your brand and get a lot of penalties if you don’t follow GDPR, HIPAA, or PCI-DSS.
Solution:
Monitor pertinent regulations within your industry. Build compliance into your software design and collaborate with lawyers or compliance specialists to verify that every element of the feature complies with applicable data protection legislation.
7. Lack of Security Expertise in the Development Team
Challenge:
An ample number of teams have gaps in their development teams that result from a lack of their knowledge of how to eliminate security vulnerabilities and risks, or how to recognize them in the first place.
Solution:
Hire software developers with experience in enterprise-grade system security because they will be more adept at the security features of the software developed. Also, make sure your existing team undergoes refresher courses on modern-day threats and guarding techniques.
Anticipating these common issues gives firms the chance to improve their cyber defenses, lower risks, and create more advanced and secure systems. Protecting one’s image, finances, and reputation can be better managed by assembling a competent group and acquiring the correct devices beforehand.
8. SQL Injection Attacks
Challenge:
Manipulating user input interfaces continues to be one of the most ruthless and earliest exploitable weaknesses to date. This can be in the form of a SQL injection which allows invaders to interact with a secure database.
Solution:
Refrain from using dynamic SQL at all costs; follow up with parameterized queries and prepared statements as they are more secure. User inputs must always be validated and sanitized and Web Application Firewalls (WAFs) should be installed to prevent common injection attacks.
Final Thoughts
The world of enterprise software security is very complex and multifaceted. Challenges range from protecting confidential information to handling third-party risk and compliance with regulations. All these challenges require attention alongside continuous evolution within the software. Proactivity through good coding standards, security auditing, threat mitigation, and applying preventative measures early—all aid in decreasing exposure and threat.
The most effective method for gaining a competitive edge is utilizing software development services that possess a thorough understanding of enterprise systems and an equally strong grasp of security protocols, tactics that are invaluable in gaining an edge. Achieving these goals starts from the bottom up through gaining a carefully selected team alongside a custom-tailored strategic plan for the particular needs of your business.
FAQs
The problems that are seen most often are data leaks, exposing harmful APIs, control access issues, weak encryption methods, and a lack of continuous security reviews. Such vulnerabilities could weaken protected information and additionally obstruct crucial business processes.
Enterprise software usually carries out functions of great magnitude as well as retains classified information. A breach in security may result in monetary loss as well as litigation while tarnishing the company’s reputation, which could threaten the organizational image. Hence, security should always be implemented right from the design stage.
Businesses can apply secure coding practices, perform regular audits, encrypt the system, integrate DevSecOps, implement role-based and access control, and guard against threats on a must-know basis to overcome major challenges in enterprise software development.
From planning and design, all the way through deployment and maintenance, security ought to be woven into the very fabric of the development lifecycle. Integrating security best practices early minimizes risks and ensures enduring protection.
Get In Touch