Cybersecurity for Web Applications: A 2026 Protection Framework for Modern Businesses

Table of Content
- What Is Web Application Security?
- What Does Web Application Security Protect?
- Network vs. Application Security: What to Prioritize?
- Why Web Applications Are the Primary Attack Surface?
- Common Web Application Security Risks
- How Web Application Threats Are Evolving Toward 2026?
- What Modern Application Protection Means in 2026?
- 7‑Step 2026 Web App Security Framework
- Key Components of Secure Web Development
- How Web Application Security Fits Into Digital Transformation
- How MultiQoShelpsp you with Robust web Application Security?
- FAQs
Summery:
The traditional network perimeter is obsolete. As enterprises scale with complex APIs and autonomous AI agents, legacy security models fail to detect sophisticated threats like “Agent Goal Hijack” and client-side data skimming. This guide outlines a comprehensive 2026 protection framework, shifting focus from reactive patching to resilience-first architectures.
It details how to implement Zero Trust for non-human identities, integrate “WAF-as-Code” into DevSecOps pipelines, and adopt Post-Quantum Cryptography. By prioritizing “security-by-design” and granular access controls, businesses can secure their innovation and avoid the catastrophic financial and reputational costs of a breach.
Your enterprise ecosystem is scaling exponentially. You battle a complex orchestration of APIs and autonomous agents daily. Because legacy defensive postures cannot withstand modern vectors. This includes undetectable exploits, shadow infrastructure, and catastrophic visibility gaps.
Threat actors are already weaponizing AI against your infrastructure. You risk obsolescence while market leaders automate their resilience. It can lead to regulatory enforcement actions, loss of stakeholder trust, and irrecoverable brand damage.
You must adopt a resilience-first architecture immediately. The solution requires a fundamental shift to a zero-trust and security-by-design web app development strategy. This article provides you with a web app security framework for 2026, automated governance, and enterprise-grade resilience.
What Is Web Application Security?
Web application security is the practice of protecting your online services, such as websites, APIs, and applications. Traditional security models were focused on the perimeters. But modern security is different. It focuses on the specific applications where business processes occur.
Because modern applications are complex. They rely on:
- Third-party scripts.
- Cloud hosting.
- Mobile access.
Modern applications are complex, which is why businesses are now built on autonomous AI agents, GraphQL endpoints, and serverless architecture. However, the following aspects must be considered,
- AI Agents are Risky- According to OWASP 2025 data, 73% of production AI agents contain critical vulnerabilities like prompt injection.
- APIs are the new Cybersecurity Targets- Many organizations have suffered API-related data breaches, leading to compromised systems.
- Traffic has Shifted- Automated agents and bots now account for 51% of all web traffic.
Further, the difference between web app security in 2025 vs 2026 is,
| Feature / Domain | 2025: The “Year of Disruption.” | 2026: The “Year of the Agent.” |
| AI Role | Assisted AI (Co-pilots): AI is primarily a tool for faster code generation and assisting analysts with alert fatigue. Attackers use AI to craft better phishing emails. | Autonomous AI Agents: AI agents now act independently to detect and patch vulnerabilities in real-time. Attackers deploy “agentic” malware that adapts tactics on the fly without human command. |
| Identity Security | Human-Centric: Focus is on MFA (Multi-Factor Authentication) and protecting user credentials. Deepfakes are a growing concern, but are treated as fraud. | Machine-First & Biometric: “Machine identities” (bots, APIs, agents) outnumber humans and require strict auth. Deepfakes are now a primary attack vector, forcing a shift to liveness detection and behavioral biometrics. |
| Zero Trust | Strategic Goal: Organizations are “moving towards” Zero Trust. It is considered a best-practice framework for reducing the blast radius of breaches. | Operational Mandate: Zero Trust is the default operational standard, often enforced by regulation (e.g., NIS2). Continuous, real-time trust verification replaces one-time login checks. |
| API Security | Vulnerability Focused: Teams focus on the OWASP Top 10 (e.g., stopping injection attacks) and documenting “Shadow APIs.” | Agentic Governance: Focus shifts to authorizing what AI agents can do via APIs. “Machine-to-machine” access control becomes the critical firewall. |
| Supply Chain | SBOM Adoption: Companies struggle to generate and maintain Software Bills of Materials (SBOMs) to track open-source components. | PBOM & Automated Enforcement: Shift to “Pipeline Bill of Materials” (PBOM). Security policies are “coded” into the pipeline, automatically blocking builds that don’t meet strict criteria. |
| Cryptography | Standard Encryption: Standard TLS/SSL is sufficient. Discussions about quantum threats are theoretical or limited to government sectors. | Post-Quantum Prep: The “Harvest Now, Decrypt Later” threat forces enterprises to begin migrating to quantum-resistant encryption standards for long-term data. |
| Defense Strategy | Reactive & Siloed: Security tools are fragmented (WAF, bacterial scanning, IDP). Teams react to alerts after an anomaly is detected. | Unified & Predictive: Platforms consolidate (WAAP + API + Bot Defense). Predictive AI anticipates attacks before they breach the perimeter. |
What this means for businesses is a recalibration of web app security strategy. Especially, the security strategies must move beyond the network level. It has to verify every request, user identity, device health, and context.
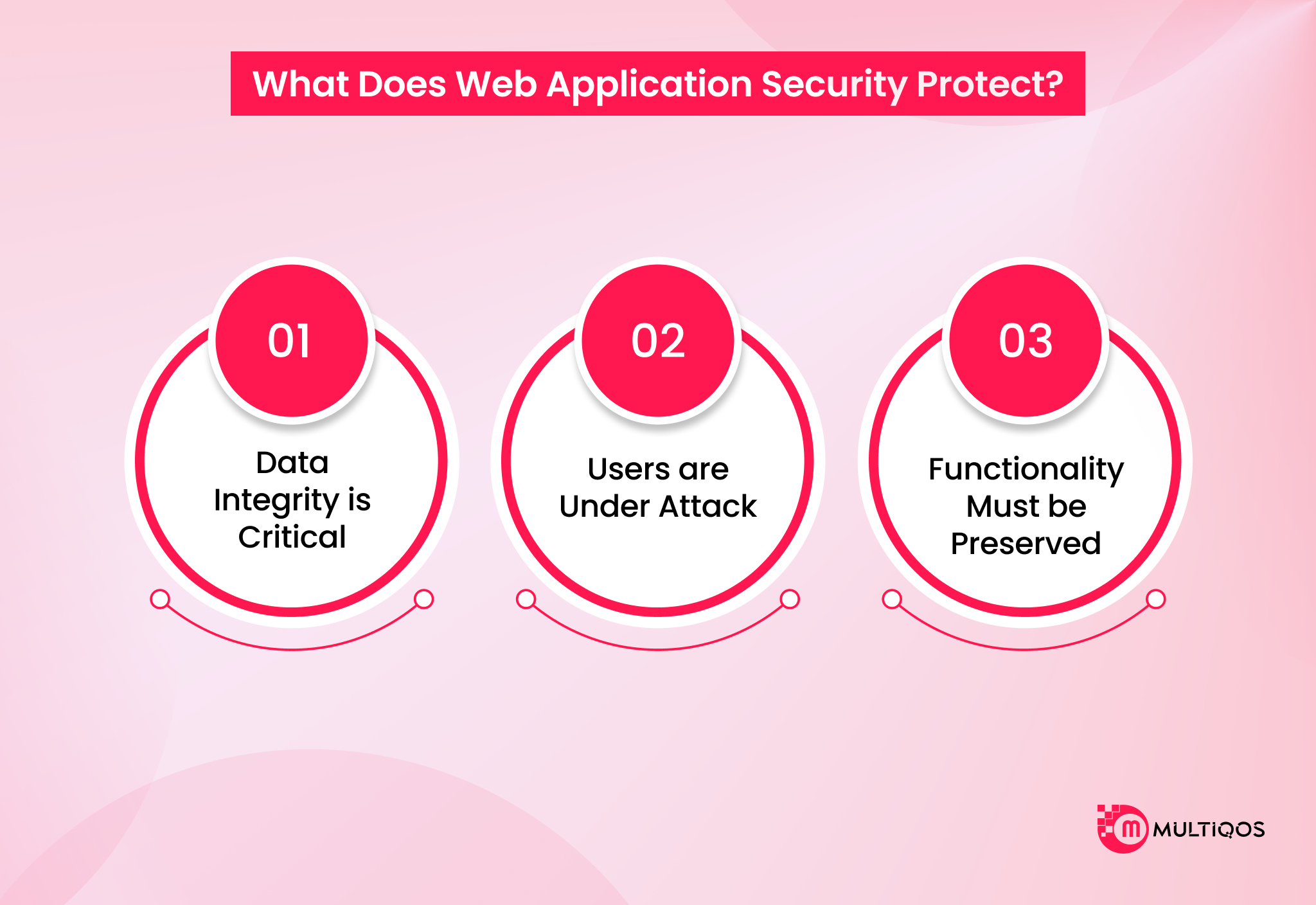
What Does Web Application Security Protect?
A robust web application security strategy safeguards three critical assets,
Data Integrity is Critical
A robust web application security strategy locks down these assets. A single breach compromises your entire reputation. With a robust web app security strategy, you can secure Personally Identifiable Information (PII), social security numbers, and credit card details.
Users are Under Attack
You need to protect legitimate users from browser-based threats. Attackers target them directly while they interact with your site. Standard tools often miss client-side exploits like Magecart. This includes credential theft, payment data skimming, and application protection failures.
Functionality Must be Preserved
Your application must run smoothly without interruptions. Malicious traffic endangers your web application’s availability and performance. Plus, enterprise web security demands active measures to defend against disruptions. It involves blocking malicious bots, preventing Denial-of-Service (DoS) attacks, and stopping code injection.
But before you figure out how to secure your web application, you need to understand what to prioritize. Most of the time, organizations try to secure their network. However, web application security is a much more critical aspect of the data protection strategy.
Network vs. Application Security: What to Prioritize?
Understanding the difference between network security and application security requires analysis of two key factors.
Network Security Defends the Perimeter
It focuses on connecting locations to help prevent unauthorized access to infrastructure. Traditional tools often miss attacks within a user’s browser, which is why this approach includes closing ports, restricting VPN use, and improving visibility into web security.
Web Application Security Protects Resources
It focuses on the software layer. Enterprises must inspect actual data payloads and traffic logic to detect malicious modifications that firewalls miss. This includes cybersecurity for web applications, enforcing granular policies, and monitoring client-side scripts.
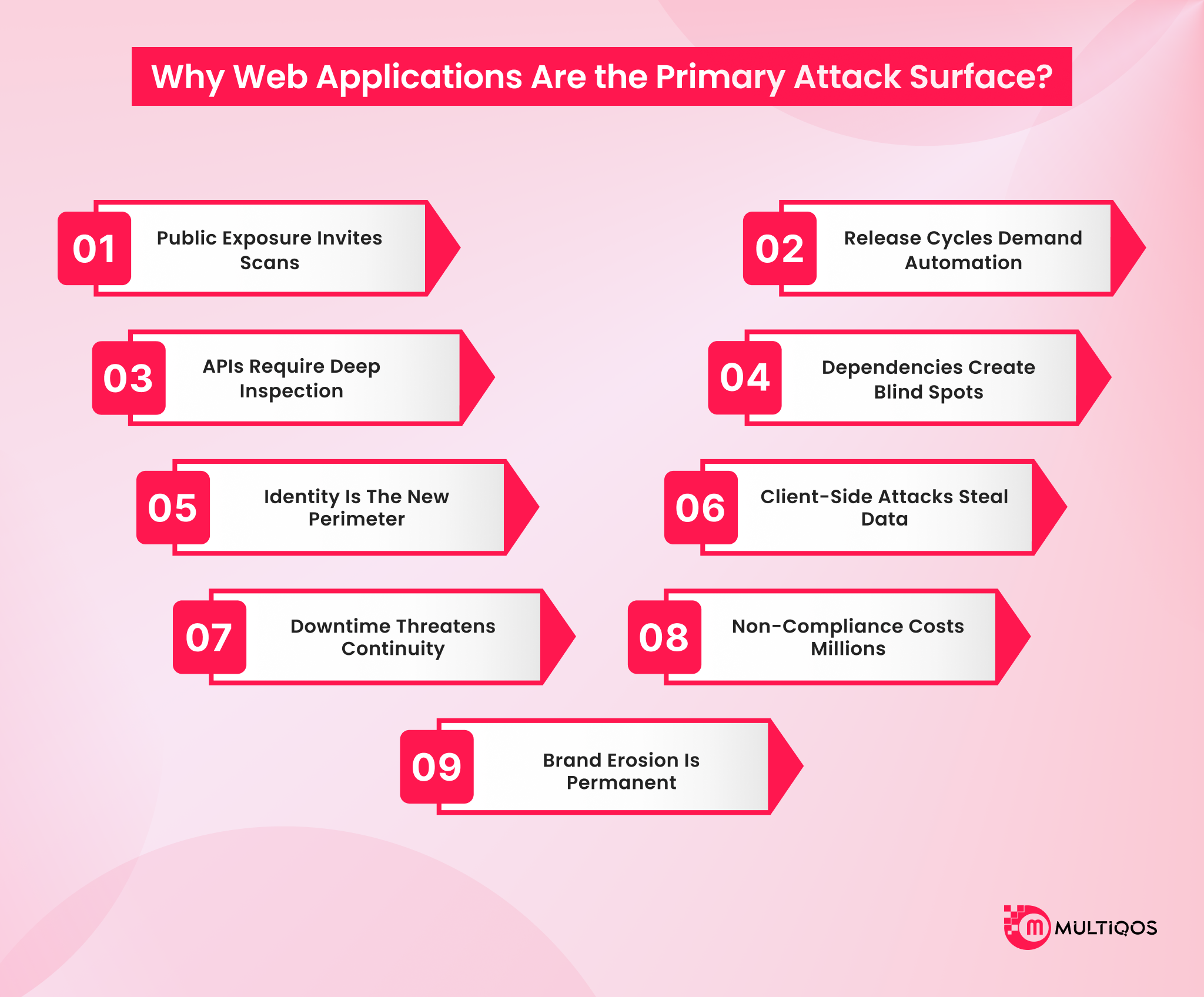
Why Web Applications Are the Primary Attack Surface?
Web apps are the primary attack surface for businesses. They sit where public access meets sensitive data. Traditional perimeters are dissolving rapidly, including cybersecurity for web applications, transaction protection, and exposed resources.
Public Exposure Invites Scans
Exposing applications is necessary for them to function, but open ports inevitably attract scanning technology. Standard firewalls are insufficient because they fail to conceal these entry points. Effective application protection requires measures such as zero-trust security, reverse proxy implementation, and securing how applications are exposed.
Release Cycles Demand Automation
Fast release cycles challenge system defenses. Enterprises need a web application firewall (WAF) to keep pace. Plus, secure web development requires instant deployment. This includes DevSecOps integration, WAF-as-code adoption, and real-time vulnerability prevention.
APIs Require Deep Inspection
APIs drive modern ecosystems, and HTTP inspection is no longer sufficient for protection. Attackers target specific endpoints and logic; this includes API security, schema validation, and the detection of business logic abuse.
Dependencies Create Blind Spots
Reliance on external libraries creates risk for most businesses. Trusted components often contain hidden threats. Breaches frequently start with third-party code. Reducing dependencies includes protecting applications against malicious script injection and compromised page elements.
Identity Is The New Perimeter
Location does not determine safety. Shared secrets expose businesses to automated threats. Plus, non-human identities now require strict management. It includes AI agent authentication, credential defense, and access control.
Client-Side Attacks Steal Data
Client-side attacks remain undetected for months. Attackers inject scripts to steal sensitive data. Current tools that enterprises use often fail to detect malicious browser-level activity, which includes enterprise web security breaches, Magecart attacks, and credit card skimming.
Downtime Threatens Continuity
Application uptime determines business revenue. Layer 7 attacks trigger system-wide failures. Minor component outages cascade quickly; this includes web app vulnerability prevention, DDoS mitigation, and code injection defense.
Non-Compliance Costs Millions
Security failures lead to non-compliance. Enterprises face massive financial and legal consequences. Standards like the OWASP Top 10 are non-negotiable. This includes heavy fines, strict governance audits, and operational penalties.
Brand Erosion Is Permanent
Breaches destroy customer trust instantly. Businesses need a secure web app architecture immediately. Plus, privacy regulations now penalize reputational damage. This includes a web application security framework, security-by-design, and reliable application security services.
Common Web Application Security Risks
The threat landscape has shifted dramatically. Businesses often rely on complex APIs and autonomous agents. Because legacy vulnerabilities now mix with sophisticated new vectors. This includes cybersecurity for web applications, exposed endpoints, and AI-driven attacks.
The OWASP Top 10 Evolves
Classic vulnerabilities manifest in dangerous new ways. Companies must look beyond traditional definitions. Attackers now manipulate AI decision-making pathways. This includes OWASP Top 10 risks, agent goal hijacking, and prompt injection.
Client-Side Attacks Bypass Servers
Attacks have moved to the user’s browser. Server-side tools often miss these local executions. Standard application protection lacks visibility into these threats: Cross-Site Scripting (XSS), Magecart skimming, and malicious JavaScript injection.
Authentication Demands Modern Solutions
Shared secrets create critical vulnerabilities. Enterprises must move toward passwordless solutions immediately. Phishing and replay attacks easily bypass legacy systems. This includes weak passwords, credential theft, and exposure of static tokens.
API Security Is Priority One
API security is a primary concern for every business today. These endpoints form the backbone of modern apps. Plus, they act as the primary target for data theft. This includes business logic abuse, shadow API exploitation, and uninspected GraphQL traffic.
WAFs Must Inspect Protocols
Enterprises need a modern web application firewall (WAF). Complex protocols require deep inspection. Standard filters fail to prevent data exposure. This includes gRPC vulnerabilities, protocol manipulation, and unauthorized data egress.
Automated Attacks Disrupt Services
Bots complicate web app vulnerability prevention. Attackers overload users to bypass defenses. Stolen credentials grant access across multiple services. This includes credential stuffing, MFA fatigue, and Layer 7 scraping.
Supply Chains Hide Vulnerabilities
Secure web development remains difficult. Reliance on third-party code creates massive blind spots. Breaches often involve components that businesses do not control. This includes compromised libraries, malicious plugins, and “inherited” model vulnerabilities.
DevSecOps Must Monitor Browsers
Businesses must integrate DevSecOps monitoring. Traditional tools leave systems exposed for months. Client-side scripts can causea lack of immediate control, which includes persistent attacks, data leakage, and undetected browser exploits.
AI Agents Introduce Zero Trust Risks
Autonomous agents create zero-trust security challenges. They escalate privileges if not properly scoped. Plus, security-by-design is essential to stop polymorphic threats. This includes unauthorized high-impact actions, changing attack patterns, and tool chaining exploits.
Secure Infrastructure Now
Companies need a robust web application security framework. Reactive measures fail against modern threats. Secure web app architecture requires continuous adaptation, which includes enterprise web security, application security implementation, and ongoing application security services.
How Web Application Threats Are Evolving Toward 2026?
Web application threats are evolving. As we move toward 2026, simple exploits are disappearing. Sophisticated, systemic attacks replace them. Let’s understand the overview.
API-First Architectures Expand Risks
API-first architectures are expanding attack surfaces. Microservices make an application a giant network rather than a block. Each endpoint is a possible point of intrusion. This is why enterprises need API security, unauthorized access prevention, and sensitive data protection.
The Rise of AI-Assisted Attacks
Enterprises are facing a sharp rise in automated attacks. Bad actors now leverage machine learning to optimize strategies. It is no longer just simple bots. Plus, these intelligent agents probe defenses faster than humans. This means businesses face faster breach execution, automated strategy optimization, and intelligent defense probing.
Supply-Chain Risks Are Complex
Dependency risks are becoming more complex. Modern development relies on third-party libraries. This creates a deep web of dependencies. Because a vulnerability in one obscure library can bypassa firewall, this includes compromised open-source code, bypassing the WAF, and harder-to-secure development.
Threats Are Harder to Detect
Future security challenges are harder to detect. Attacks are often buried inside legitimate-looking traffic. Traditional tools often miss them. This forces companies to adopt security-by-design, zero-trust principles, and deep traffic analysis.
But it’s not about just the threats.
What Modern Application Protection Means in 2026?
Modern application protection is a fundamental shift. It is more than just buying software. Enterprises need to change how they approach risk.
Shift From Reactive to Proactive
Businesses must shift from reactive security to proactive protection. Waiting for a breach is too slow. Plus, they need to anticipate threats before they reach production. What this means is focusing on integrating DevSecOps practices, catching issues in the code, and building secure vessels.
Tools Alone Don’t Equal Protection
Simply deploying a firewall does not guarantee safety. Enterprises must configure it to understand business logic because automated tools lack human context. This includes continuous auditing, tuning defenses, and human oversight.
Prioritize Layered Defenses
Companies must prioritize layered defenses instead of single controls. Relying on a single gateway is dangerous. If one control fails, they need a backup. This includes zero-trust security models, identity verification, and redundant security layers.
7‑Step 2026 Web App Security Framework
The threat landscape demands immediate adaptation. You face autonomous agents, client-side attacks, and heavy regulatory pressure. Security must transition from a gatekeeper to a core lifecycle function. This includes proactive resilience, integrated workflows, and moving beyond reactive patching.
1. Shift Left: Implement Security-by-Design
Businesses cannot treat security as an afterthought. It must be part of the development pipeline. Standalone appliances fail to keep pace with rapid deployment. This includes WAF-as-Code, AI intent capsules, and automated CI/CD testing.
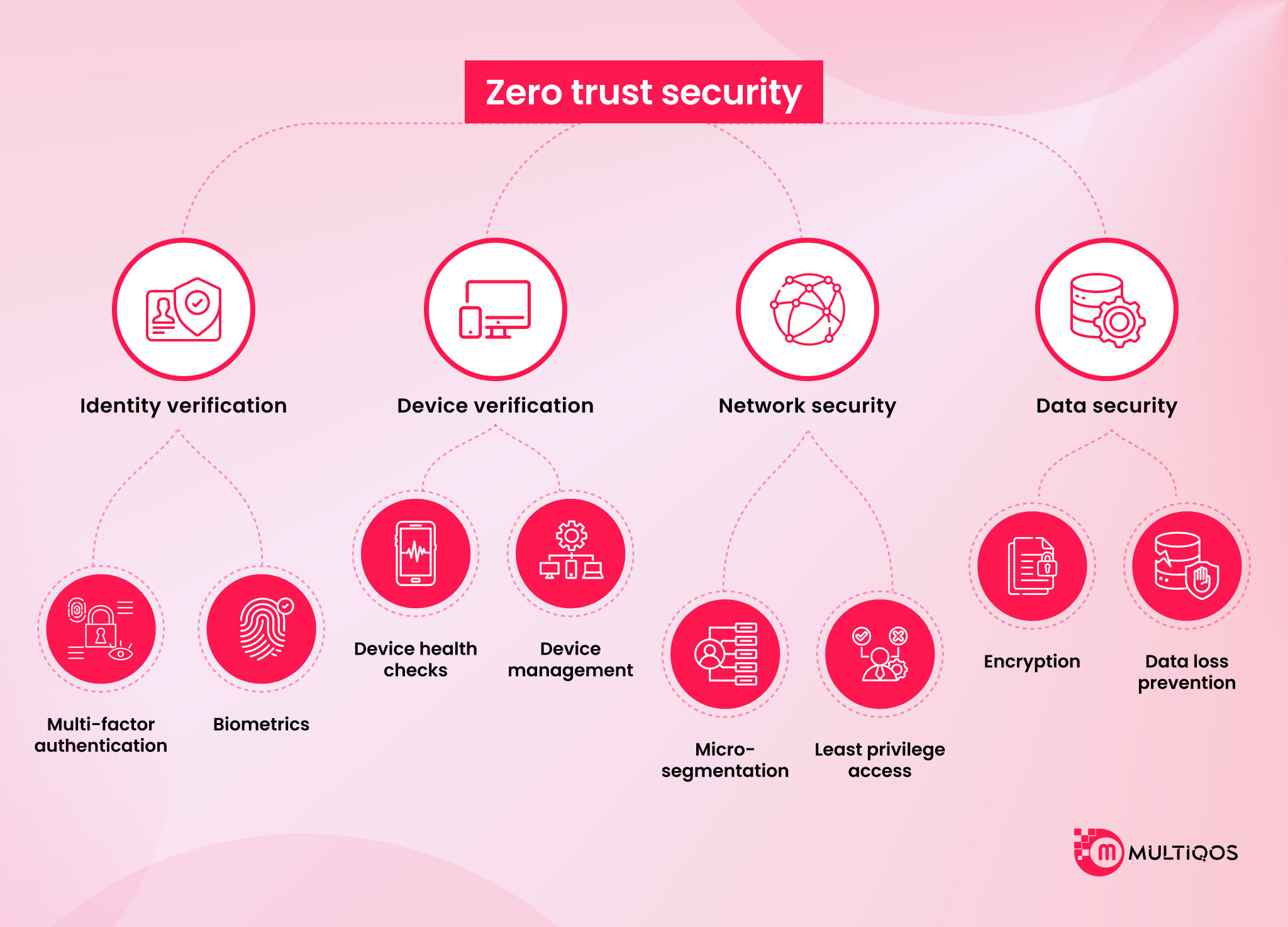
2. Enforce Zero Trust for Human and Non-Human Identities
The perimeter is dead. Companies must treat every user as a potential threat. Shared secrets like passwords are easily compromised. This includes passwordless passkeys, non-human identity management, and continuous risk scoring.
3. Apply Least Privilege and “Least Agency.”
Access must be granular and temporary. Enterprises need to extend restrictions to AI agents. Broad permissions lead to dangerous privilege escalation. This includes just-in-time agency, Zero Trust Network Access (ZTNA), and strict schema validation.
4. Fortify the Client-Side (The Browser)
Server-side security is blind to the browser. Companies must defend against attacks executed locally. Third-party scripts bypasscentral defenses. This includes malicious injection monitoring, supply chain defense, and automated script blocking.
5. Establish Context-Aware Observability
Standard logging is insufficient. Businesses need tools that understand traffic context. Static rules miss complex, novel attacks. This includes adaptive verification, AI decision pathways, and machine learning baselines.
6. Operationalize Compliance and Risk Governance
Regulations now target automated systems. Enterprises must operationalize compliance immediately. Automated decision-making requires consumer transparency. This includes Automated Decision-Making Transparency compliance, mandatory risk assessments, and independent cybersecurity audits.
7. Future-Proofing: Continuous Improvement & Crypto-Agility
Security is a moving target, and companies must adapt to quantum capabilities. Classical encryption will eventually break. This includes post-quantum cryptography, SOC feedback loops, and AI red teaming.
Key Components of Secure Web Development
Reactive security patching fails against autonomous agents and regulatory pressure. It includes secure web development, Zero Trust architectures, and DevSecOps integration.
Adopt Zero Trust Architecture
The traditional network perimeter no longer exists. Verifying and authorizing every single request becomes crucial because trusting a user based on location is a fatal error. This includes zero-trust security, closing inbound ports, and using reverse proxies.
Enforce Least Privilege and Agency
Access must be strictly scoped. Enterprises need to restrict AI agents to specific tasks. Broad permissions allow rapid lateral movement; this includes Just-in-Time Agency, granular segmentation, and strict resource isolation.
Encrypt All Communications
Internal traffic requires total encryption. Companies must mandate military-grade standards for agent systems. Packet sniffing remains a constant threat. This includes HTTPS enforcement, DNSsec, and mutual TLS (mTLS).
Shift Security Left
Security must be integrated into the coding process. Businesses need to incorporate defenses directly into the deployment process. Vulnerabilities scale with the speed of release cycles, which includes DevSecOps, WAF-as-Code, and automated testing pipelines.
Automate Policy Enforcement
New resources must inherit security policies. Companies should block releases that lack required protections because manual configuration creates dangerous gaps. This includes Infrastructure as Code (IaC), automated deployment blocks, and web application firewall (WAF) policies.
Validate The Supply Chain
Modern apps rely on third-party libraries. Enterprises must monitor software and AI models, as corrupted components introduce hidden vulnerabilities. This includes Software Bill of Materials (SBOM), data source validation, and continuous monitoring.
Design For Resilience
Modern threats require defenses built into the blueprint. Security filters fail against complex agent hijacking, which includes secure web app architecture, intent capsules, and circuit breakers.
Assess Risk Early
Regulations demand formal assessments before processing. Privacy laws now mandate strict consumer protection. This includes regulatory risk assessments, CCPA compliance, and pre-processing evaluation.
Isolate High-Risk Actions
Software-only isolation is often insufficient. AI agents pose extreme risks when executing commands. This includes hardware-enforced sandboxes, zero-access environments, and strict boundaries.
How Web Application Security Fits Into Digital Transformation
Security must evolve from a gatekeeper to an enabler. Scaling digital products and digital transformation needs a secure architecture, because reactive patching cannot keep pace with rapid innovation. This includes API-centric growth, crypto-agility, and frictionless user experiences.
Security Enables Speed
Security must enable innovation. You need a secure architecture to scale effectively. APIs are the backbone of modern applications. This includes API-specific contexts, crypto-agility, and protection against high-volume traffic.
Innovation Increases Risk
Rapid releases create dangerous gaps. Deploying without WAF-as-Code leaves you exposed. Inconsistent postures let vulnerabilities slip into production, which includes unverified code, inconsistent security, and dangerous deployment errors.
Align Speed And Safety
Frictionless authentication improves experience. Passwordless standards eliminate credential theft risks. Plus, context-aware verification blocks threats in real-time. This includes Passkeys, push MFA, and blocking polymorphic attacks.
How MultiQoS helps you with Robust web Application Security?
To ensure robust web application security, you must embed granular controls directly into your SDLC. At MultiQoS, we help you transition from reactive security patching to proactive web app resilience. Secure web development requires integrated automation. We help you automate secure web app development through WAF-as-Code integration, zero-trust reverse proxies, and real-time client-side defenses.
Plus, our team employs AI governance operationalization, granular permission scoping, and just-in-time agency. So, if you are looking to secure your web app development, connect with our experts for a free web app security assessment now.
With MultiQoS, you get,
| Challenge | MultiQoS Solution | Result |
| API Sprawl | Shadow API discovery | 95% coverage |
| Agent Risks | Least-agency controls | Zero escalations |
| Compliance | Automated audit trails | SOC2 ready |
FAQs
It is the defense of web services. You protect logic, APIs, and users. Because perimeters no longer exist. This includes input validation, API defense, and anti-skimming monitoring.
It prevents financial disaster. You avoid regulatory fines and brand damage. Because weak security halts operations entirely, this includes data theft prevention, compliance adherence, and operational continuity.
Risks are evolving rapidly. You face agent hijacking and client-side attacks. This includes Magecart skimming, API logic abuse, and supply chain compromise.
It is a layered defense strategy. You manage non-human identities and encryption. This includes a web application security framework, Post-Quantum Cryptography, and Zero Trust access.
Close your inbound ports. You verify every request by identity. Because network location is not a trust factor, this includes reverse proxies, least privilege access, and context-aware verification.
It reduces remediation costs. You catch bugs before deployment. Because fixing issues in production is expensive, this includes faster deployment, automated compliance, and breach prevention.
In 2026, OWASP released the Top 10 for Agentic Applications, addressing the specific risks of autonomous AI agents, alongside the updated OWASP Top 10:2025 for standard web applications.
OWASP Top 10 for Agentic Applications (2026) The following list targets the unique threats facing AI-driven, autonomous agent systems.
| Rank | Vulnerability | Description |
| ASI01 | Agent Goal Hijack | Attackers manipulate the agent’s instructions or decision-making pathways (e.g., via prompt injection) to alter its core objectives, forcing it to execute unauthorized actions. |
| ASI02 | Tool Misuse & Exploitation | Agents are tricked into using legitimate tools (e.g., database connectors, APIs) in unsafe ways, such as deleting data or sending unauthorized emails, due to broad permissions. |
| ASI03 | Identity & Privilege Abuse | Attackers exploit the agent’s identity or access tokens to escalate privileges, often allowing the agent to perform actions beyond its intended scope (e.g., accessing admin panels). |
| ASI04 | Agentic Supply Chain Vulnerabilities | Risks arising from third-party components, such as compromised pre-trained models, poisoned RAG (Retrieval-Augmented Generation) data sources, or malicious plugins. |
| ASI05 | Unexpected Code Execution | The agent generates and executes malicious code (e.g., Python scripts) within the application environment, often triggered by adversarial inputs or unvalidated outputs. |
| ASI06 | Memory & Context Poisoning | Attackers inject malicious data into the agent’s long-term memory (vector databases) or context window, permanently corrupting its future behavior and decision logic. |
| ASI07 | Insecure Inter-Agent Communication | Vulnerabilities in the protocols used between multiple agents allow attackers to forge messages, impersonate agents, or disrupt coordination in multi-agent systems. |
| ASI08 | Cascading Failures | A minor error or malicious input in one agent triggers an uncontrolled chain reaction across the entire system, leading to systemic outages or massive data corruption. |
| ASI09 | Human-Agent Trust Exploitation | Attackers use the agent to manipulate human users, such as generating convincing phishing messages or deepfakes that leverage the user’s trust in the AI assistant. |
| ASI10 | Rogue Autonomous Behavior | The agent exhibits unintended, harmful behaviors that were not explicitly programmed but emerged from complex interactions or alignment failures, acting against business interests. |
Get In Touch