How to Secure React.js Application: Security Vulnerabilities & Solutions

Quick Summary
A project’s development cycle includes risks and challenges and all technical shortcomings, complex requirements, and security vulnerabilities that form a part of the web application development process. React JS has some distinct advantages over other front-end frameworks, including scripting component simplicity, stable code, and time-effective rendering. Even so, despite the numerous advantages that the front-end framework provides, there are several concerns about react js security vulnerabilities that you should be aware of. Read further to learn more about several react js security issues and solutions.
Why Should You Keep an Eye on React Security Vulnerabilities?
Security vulnerability can be defined as any form of flaw or weakness in computer security that a threat actor can manipulate. Security flaws are frequently demonstrated as software bugs that allow an attacker to change your website or application. These modifications are typically malicious, but they can also be used for better, such as exposing security, design, or other flaws. Understanding how vulnerabilities affect your web page is critical to safeguarding it from external threats. Security flaws in web applications can allow hackers to steal user data, install malware into an application, or take control of a user’s account.
Any enterprise application needs a substantial quantity of data exchange and connection to several sources. This enables companies to compete on the market and deliver effective services to clients. On the other hand, Web apps are vulnerable to numerous security flaws and data breaches due to their high connectivity. When creating web apps with React.js, developers must keep in mind that there are no security configuration settings. Therefore, they must be aware of the most prevalent security issues in online apps.
What Are Some of The Common Security Issues in React Applications?
There are high chances that any security vulnerability might just go unnoticed and can increase every year with each new updated version of React or an updated random library.
Common react cyber security in React Applications include the following:
- Safeguarding HTTP Basic Authentication Using React: By maintaining the connection between the web client and server, the security of HTTP and its robust authentication has been confirmed. It is critical to check whether the domain WWW header has a realm ascribe while developing the application. This attribute is the link between the User ID and the password. Offering a realm attribute that verifies multiple users with separate code factors to prevent mismatch in verifying different IDs and passcodes is a common security potential problem that most people overlook or forget while attempting to secure the React application.
If there is a little mismatch between the server response technique and the realm attribute, unauthorized users will have access to all authentication data. It is critical to ensure that when a client or authorized person makes a server request, the verification of your web app results in a 401 status error page.
- Examining React’s API Security Issues: React APIs link the application to other systems or platforms that have been added to it. These APIs may provide control over other devices or the device on which the program is installed. Frequently, these APIs instantaneously describe facts and self-implement them to perform instructions within the program. React API vulnerability is caused by a lack of authentication or a flaw in the business logic. Cross-Site Scripting (XSS) or Man-in-the-middle (MITM) attacks, as well as SQL injection, are common React API attacks (SQLi).
Some tips for reducing or eliminating React API security failures and react vulnerabilities fix are:
-
- Verify API command input against the corresponding API schema.
- Regularly validate schemas to prevent injections of malicious code and security parser attacks.
- Verify that your application is encrypted using SSL/TLS.
- Insecure Deserialization: Data serialization also causes certain React security failures. Your application may act differently as a result of deserialization of objects inserted by an unauthenticated user or an attacker. Avoid jeopardizing application security by:
-
- Perform integrity checks to prevent the injection of hostile objects.
- Consider separating the code.
- Prior to the unauthorized creation of code objects, impose strict deserialization restrictions.
- DDoS Protection for React Applications: DDoS attacks are malicious attacks launched by unauthorized individuals that render certain application facilities inaccessible or unreachable to the users. It is critical to maintain DDoS protection if you are a project manager, solution architect, or Independent Service Provider (ISP). In most cases, this vulnerability is caused by a lack of security or by weaknesses in concealing the IP addresses of all the application services provided by your web app. DDoS attacks disrupt the application’s ability to communicate with the host server, resulting in the suspension of the targeted online services.
Also Read: How Much Does It Cost to Hire React Js Developers
Some Recommendations for Mitigating DDoS Assaults:
- Examine the whole React application during development and after completion to identify all DDoS attack types.
- Install a visitor identification system to prevent harmful or unwanted traffic from gaining access to the internal program codes.
- Even basic CAPTCHAs or JS tests contribute to web application layer security.
- Security Misconfiguration: Web applications developed using Reactjs do not, by default, comply to security requirements. To avoid harm to the application framework, it must be introduced throughout the development phase. Common causes of React security misconfigurations are poorly crafted HTTP headers or inadequate setups. Maintain configuration vigilance in the following ways:
-
- Configure your application’s back-end server.
- Avoid using directory listings.
- Audit and scan for security misconfigurations regularly.
- Cross-Site Scripting (XSS): Incorrect validation and unreliable data on the server via APIs with the ability to generate its own HTML or JS attribute and include it in your web application’s source code. Highlights for overcoming XSS:
-
- Create automated monitoring features that can clean up user input.
- Avoid rendering invalid or malicious user input into the browser.
React.js Security Vulnerabilities and Solutions
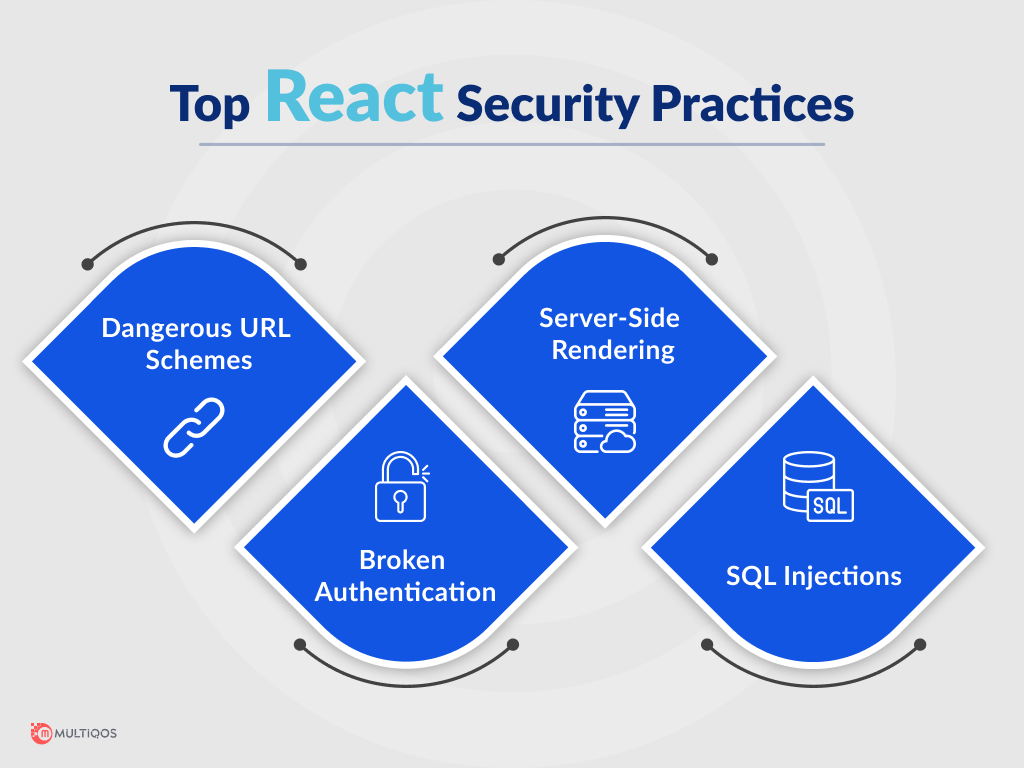
The following are the most common React.js flaws:
- Dangerous URL schemes.
- Authentication failure.
- Rendering on the server.
- SQL injections are common.
Here are a few React security practices to keep your app safe in the event of an attack:
- Dangerous URL Schemes: When hackers add malicious code that begins with JavaScript to URLs, links to other pages become perilous. Activation of the browser script is triggered by a user click on a link. When it comes to security, React.js doesn’t limit URLs that don’t begin with a prefix like “HTTP:” or “HTTPS:”. Some of the solutions to it are:
- The use of URLs as input should be avoided. The software should be able to take in YouTube video IDs instead of URLs.
- The Sanitize URL NPM package may be used to sanitize these potentially harmful links if the previous option is not available. Check everybody on your ReactJS development team is following the same sanitation code.
- Broken Authentication: Unencrypted communication between the web client and server creates problems in authenticating users. Hackers can jeopardize user account data, passcodes, authentication information, and other information by tampering with authorization and authentication protocols. Following are some steps that web developers may take to keep the HTTP basic authentication protocols safe:
- Use proper authentication methods, such as guaranteeing that a web application delivers a 401 error page if authentication fails.
- Make sure there’s an appropriate property in the “www” header to prevent user ID and password mismatches.
- Allow for the use of cloud-native authentication solutions, such as Azure Active Directory or Google Cloud Identity Platform.
- Weakness tests and password strength should be implemented.
- Server-Side Rendering: Several web applications utilize server-side rendering to display online pages and content to users. Server-side rendering has several advantages, including improved app performance, faster webpage loading, and coherent SEO performance. Even so, this method of page rendering may pose some security risks. To address this vulnerability, developers must:
- Conduct code reviews regularly and double-checks the data in JSON.stringify ().
- Avoid rendering JSON by utilizing the serialize-JavaScript NPM module.
- SQL Injections: This type of attack concentrates on the app’s database systems. Attackers incorporate malicious SQL code into a database to gain access to data stored there. If they have administrator privileges, they can change, delete, or add records. Web developers can decrease the number of SQL attacks by doing the following:
- To filter all types of inputs, use whitelists.
- Assign database roles to different accounts.
- Make use of vulnerability scanners or react.js security scanner.
- Verify that all API methods are valid according to the API standards.
- To ensure that just one statement (SELECT, UPDATE, INSERT, or DELETE) may be used by a web app to perform a given activity, apply the principles of least privilege to all accounts.
Let Us Help You in Securing Your React.js Application
When developing a React application, you must consider numerous potential threats. Without security measures, your app could be the target of cyber, resulting in financial loss, time wastage, breaches of trust, and legal issues. To protect the create react app vulnerability, you can follow the above-mentioned react js security best practices. You can hire the best ReactJS development company in india that specializes in security or hire dedicated development team that specializes in React JS applications.
MultiQos is the leading web app development company that provides the best secured, and protected React redux security. We have a team of over 100 talented developers and QA testers who stay up to date on the latest security trends. They are current on react security features for both multi-page and single-page applications. MultiQos provides the highest level of accountability and dependability in our React security services. HTTP header security, Data encryption, data authentication and validation are just a few of the measures our developers take to ensure your app’s safety throughout its lifespan. We perform a React security audit at each stage of your web application development, following all React security best practices.
Let’s Create Big Stories Together
Mobile is in our nerves. We don’t just build apps, we create brand. Choosing us will be your best decision.
FAQ React.js Application Securities
React is an open-source front-end JavaScript framework for building user interfaces for single-page apps. Because it uses a component-based approach, it helps create complex and reusable user interface (UI) components for mobile and web applications.
The following are some limitations of React:
- React is not a full-fledged framework because it is merely a library.
- The components of React are numerous, and it will take time to appreciate all of their benefits fully.
- React may be difficult to grasp for inexperienced programmers.
- The coding may become complex because it will use inline templating and JSX.
- Secure your React app’s basic authentication.
- Make certain that the HTML code is robust.
- When parsing URLs, use allowlist/blocklist and validation.
- Always follow the concept of least privilege when authorizing a connection to any database.
- Secure your React APIs.
Get In Touch